
Multi-cloud deployments lead to network complexity that needs future-ready security to arm against cyber threats
The biggest post-pandemic business need is to provide seamless digital experiences. Organizations have realized that minimizing operational costs, achieving scalability and offering flexibility are the three main cogs in the digitization and optimization wheel, as the world moves into a turbulent yet promising future.
In short, the answer is to embrace the cloud, not just for storing and retrieving data, but also as an infrastructure for all-round computing. In the race to become cloud-enabled, businesses are increasingly integrating multi-cloud capabilities into their core operational IT. But this comes at a price.
The complexity challenge
The total number of mission-critical applications running on public clouds has doubled in the last two years, and this has brought to the brim, the rather grim reality of inadequate security. Benefits of multi-cloud deployments come at the price of dramatically increased network complexity, which in turn requires you to have robust protocols and strategies to mitigate risks from cyber threats and data compromise. In other words, the 3 Ws of an enterprise – Workforce, Workplace and Workload need to become secure and impenetrable:
Workforce – A distributed workforce that can access any IT asset from anywhere needs to be protected from cyber threats.
Workload – Distributed micro-services architecture-based application workload could be running anywhere from edge to cloud. Such applications need to run on a secure environment.
Workplace – Employees working from anywhere, using any device, need to be protected from cyber threats.
The need to acknowledge multi-cloud vulnerabilities
The favourite vulnerabilities for any cyber attacker are misconfiguration, poor encryption, flawed key management, insufficient credential management, and insecure APIs. Attackers can also breach data in a multi-cloud environment due to inconsistent security protocols at the Cloud Service Providers (CSP) end. The first step to eliminating threat is to articulate the challenge, and for any business, the five main points of leakage around multi-cloud security are:
Each of these require specialized interventions and strategies to successfully combat them:
Configuration errors and inconsistent policies: One common security issue that businesses make while migrating workloads to the cloud is misconfiguration of security and privacy settings. An important way to prevent and mitigate human error is through automation. Automated configuration management tools can reduce the role of humans from the configuration process, and additional automated error checking and security monitoring tools can catch and fix issues before production.
Dynamic user access controls: Multi cloud environments make user access control management increasingly complex and challenging. Though cloud providers have in-built controls for managing user authorization and access privileges, a multi cloud strategy would require maintaining multiple user access systems simultaneously. Keeping consistent policies across multiple platforms without a centralized control system is a huge logistical challenge. For a successful multi cloud security strategy, you need a central framework that supports all of cloud platforms and allows to apply security and access policies across the board.
Workload freshness: Patch management and workload freshness are vital to any security strategy. Systems need to stay up-to-date to ensure any known vulnerabilities are patched, and workloads must use the most recent version of any dependencies. In a multi cloud environment, one need to contend with the specific vulnerabilities, patch schedules, and update procedures of each individual platform, and ensure that all cloud instances are on the same version. This is where a centralized multi cloud management solution can help, by monitoring all of cloud systems and tracking updates so that all involved can easily apply patches and perform refreshes.
360degree Visibility: Visibility is a major issue with cloud security, which is further amplified by multi cloud strategies. When we use a third-party cloud provider, we may not have access to every layer in the cloud computing stack by default, which means we don’t have visibility on all security flaws or vulnerabilities. Though cloud providers often offer some means of in-built monitoring on their services, it may not give us full visibility or granular logging. To gain full visibility on multi cloud architecture, we need a centralized cloud security posture monitoring and workload protection solution that is compatible with all platforms.
Shared Security Model: While operating on the cloud, the shared security model means that CIO is responsible for certain aspects of cloud security while the service provider is responsible for the rest. Exactly where this line is drawn can vary from provider to provider, so we can’t assume that every platform in your multi cloud environment provides the same level of security. We can use a multi cloud management solution to help you track the security requirements of each individual provider and set the appropriate controls. Another strategy is to determine which service requires us to assume the most responsibility for our cloud security, and then use multi cloud management to apply those policies and controls across the board.
Three step solution to achieve impenetrable security
Keeping in mind, the five big challenges of multi-cloud deployments, businesses can truly transform their operations, while staying flexible, seamless and secure, just by fine-tuning their security philosophy to include three critical aspects of cloud-enabled IT:
Automation: Automating end-to-end security is also going to play a major role in our multi cloud security strategy. The more potential points of human error we can eliminate, the better, especially in a highly complex multi cloud environment. This maximizes threat detection and incident response processes while minimizing the chances of costly mistakes.
Visibility : It is a massive challenge for security professionals to maintain visibility while enforcing a consistent security policy across the entire environment. It is important to deploy a solution that synchronizes all alerts, traffic, security tools and cloud-based data in a single framework so you can easily maintain visibility across network, perform analysis and ensure compliance violations are audited in real-time.
Stronger User access control: multi-cloud deployments are increasingly creating the need for newer and more advanced identity and access management solutions to meet the needs across both private and public cloud environments. Apps run across multiple clouds, consequently, user identities are distributed across multiple clouds to provide appropriate user access for separate applications in complex environments. This increases the need for solutions such as two-factor authentication (2FA), multi-factor authentication (MFA), and single sign-on (SSO).
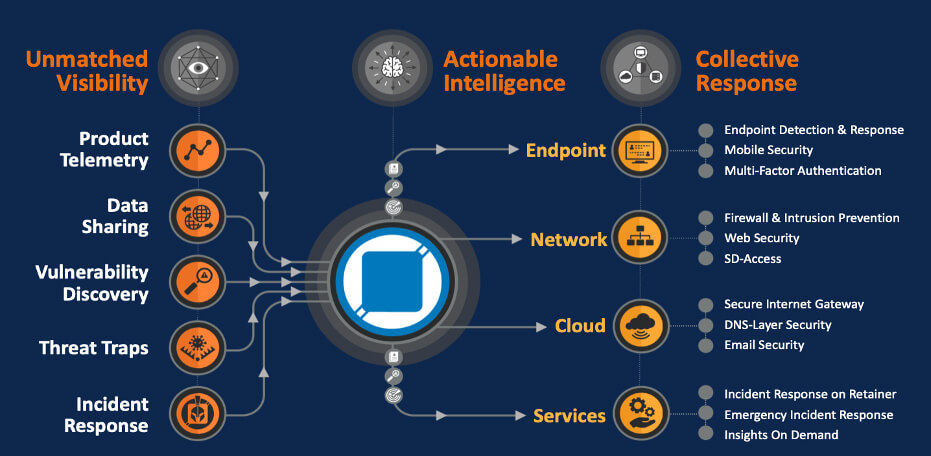
Mitigating threats while toggling between users, service providers and applications and building a robust framework is now possible with impenetrable security as shown above. This framework that includes specialized features and data sovereignty has been deployed time and again with great success